This blog excerpt is taken from our July 2023 newsletter. To view the rest of the newsletter, visit rmf.org/newsletter.
By Kathryn Daily, CISSP, CGRC (Formerly CAP), RDRP
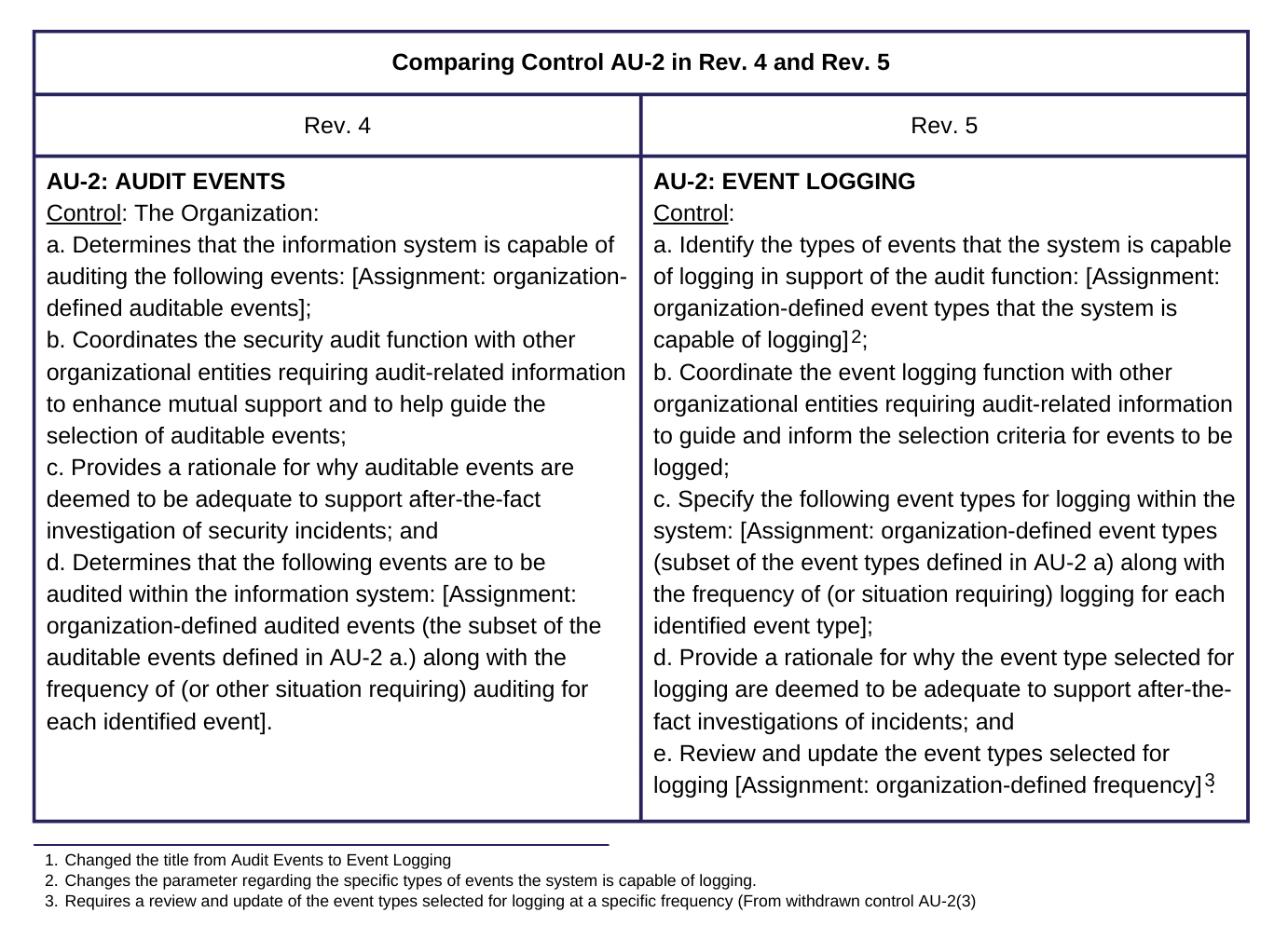
NIST SP 800-53 (National Institute of Standards and Technology Special Publication 800-53) provides a set of security and privacy controls for information systems and organizations. It was initially developed by NIST thanks to the E-Government Act of 2002, or more specifically, the Federal Information Security Management Act (FISMA) passed on December 17th, 2002. This control set has evolved many times over the years, and in September 2020, NIST released Rev. 5.
The main difference between NIST SP 800-53 Rev 4 and Rev 5 is the update and enhancement of the controls framework to address privacy alongside security, rather than tacking it on at the end, as has arguably been done in previous years. Here are some key differences:
1. 269 new controls and 2 new families
Rev. 5 introduces 65 new base controls and 204 control enhancements. 28 of these controls are assigned to the moderate baseline. Many of those new controls come from the two new families to wit, Supply Chain (SR) and Personally Identifiable Information Processing and Transparency (PT) – More to follow.
2. Consolidating the Control Catalog
Rather than having a separate appendix (J) for privacy controls, Rev. 5 has integrated the privacy controls into its own distinct family (PT – Personally Identifiable Information Processing and Transparency) and the existing PM – Program Management family. Additionally, some privacy controls were also incorporated into current security controls, allowing the controls to serve both security and privacy and achieving more efficient control implementation. One example of a privacy control having been integrated into a previous security control is the inclusion of privacy training elements in the AT family.
3. Integrating supply chain risk management
Rev. 5 has established a new family of controls focused on supply chain risk management to ensure that security and privacy requirements, threats, and other concerns are addressed throughout the system development lifecycle and the supply chain. Both government (at all levels) and industry now have a much larger focus on supply chain threats and NIST has responded by including the controls required for organizations to effectively manage that risk.
4. Adding new state-of-the-practice controls
800-53 was last updated in 2015. A lot has changed since then. Granted, Rev. 5 came out in 2020 and a lot has changed since even then, but I digress. Many new controls have been added to reflect evolving cyber threats and new safeguards and countermeasures that have become available. One such control is IA-12, Identity Proofing. Historically, online identity has been managed with usernames, email addresses, and passwords. Today, the concept of a user identity is far more complex. Identities now encompass layers of information and verification including physical identification documents, knowledge-based security questions, biometrics, etc. Identity proofing allows organizations to better secure users and their data by verifying the identity of individuals with a much higher level of accuracy.
5. Making controls outcome based
Rev. 5 has removed the entity responsible for satisfying the control (i.e., information system, organization, etc.). This puts the focus on the protection outcome to be achieved by the application of the control. For example, changes to IA-4 Identifier Management:
Rev 4 states, “the organization manages information system identifiers by:”
Rev 5 removes “the organization” and simply states, “manage system identifiers by:”
6. Clarifying and defining relationships
Revision 5 clarifies the relationship between requirements and controls as well as the relationship between security and privacy controls in Chapter 2.
7. Separating the control selection processes from the controls
The control selection process was moved from the 800-53, to the 800-53B. The intent with this change was to develop the control catalog as a stand-alone document to enable use by different communities of interest. The control set is technology-neutral, and the guidelines can be adopted by any organization operating an information system with sensitive or regulated data. Many frameworks use the 800-53 control set including the obvious Risk Management Framework used by federal agencies and the Department of Defense.
Additionally, DFARS 7012/NIST SP 800-171 which is used by all companies in the defense industrial base that use controlled unclassified information use the 800-53 Control Catalog. The controls also map to other frameworks such as CSF, PCI DSS, and HIPAA. Even organizations that aren’t using a specific framework can create their own baseline based on their internal risk assessment to address the identified residual risk.
8. Transferring control baselines and tailoring guidance to NIST SP 800-53B
The High, Moderate, and Low baselines were also moved to the 800-53B to allow the 800-53 control catalog to be used by different communities of interest as the baselines are applicable to federal agencies and reflect specific requirements under FISMA and OMB A-130.
9. Removed “Federal” from the title of the document
In Rev. 5, the word “Federal” was removed from the title. This change was made to reinforce the efforts of widespread adoption by the public and private sector. While only federal systems require the NIST framework, many voluntary frameworks either exclusively use the control set, or have mappings to the 800-53 control set. It’s very likely that in future revisions, many of the frameworks not currently based on the 800-53, will be altered to align with it.