By Marilyn Fritz, CISSP
Cybersecurity is notoriously challenging, with every new day bringing more media stories about losses from endless breaches. Beleaguered cybersecurity professionals are left coping with the onslaught and, more often than not, pleading for resources. Leaders in both private and public sectors all around the globe are hammered with conflicting requests for resources. Cybersecurity outcomes can be nebulous, at best. So how to decide which wins? How are the priorities established? What works?
This is where any cybersecurity framework comes in… And where “The” (NIST) Cybersecurity Framework shines. So what is “It” (the NIST Cybersecurity Framework, or “CSF”)? Before going down that path, know that there are a number of cybersecurity frameworks – each with varying degrees of global deployment. Leading examples include ISO 27001, COBIT, and NIST’s other (mega) NIST Risk Management Framework (RMF), which leverages NIST SP 800-53 controls. A security framework is intended to guide the management and implementation of security programs and associated controls. Basically, all frameworks consist of a set of processes and information security control sets (think anti-virus, back-ups, awareness, and training) that align strategy with implementation in an effort to define priorities for resource allocation that mitigate risk. However, the challenge often lies in how to understand the security posture of organizations that have implemented different frameworks. This is one place that the CSF does a pretty good job. That is, the CSF can be used as an overlay, or translator, for other, disparate cybersecurity frameworks. Or, it can serve independently.
Originally intended for critical infrastructure (“basic survival systems” such as healthcare, financial, energy, communications, among others), the CSF flexibility, common language, and potential rigor have been a boon to its adoption. It can be implemented with relative ease irrespective of the environment, and executives appreciate the value of a framework that they can understand. This has speeded the path for global adoption – and the CSF is breaking records on that score.
The CSF was developed by the National Institute for Standards in Technology (NIST), an agency of the U.S. Department of Commerce. The NIST mission is to promote innovation and industrial competitiveness. It is the same agency that created the rigorous Risk Management Framework, or “RMF”, mandated by the President for use by the U.S. Department of Defense (DoD) and Federal government information systems. So NIST has credibility. Furthermore, the CSF leverage the same NIST SP 800-53 information security control set used by the RMF. It gets better because the CSF was created with ongoing, extensive collaboration among multiple representatives in the private and public sector. It is also current, with regular updates to address evolving threats such as supply chain risk management (SCRM), and Internet of Things (IoT) and artificial intelligence (AI) – to name a few.
As with any such framework, the CSF lays out an iterative process for identifying and mitigating cybersecurity risk. The CSF does present its own language, but is readily recognized to match with terminology in other, more established frameworks, and is relatively easy for those who hold the purse strings to understand, even the occasional luddite. The CSF consists of an iterative 7-step model for “Establishing or Improving a Cybersecurity Program.” These are: 1. Prioritize and Scope; 2.Orient; 3. Create a Current Profile; 4.Conduct a Risk Assessment; 5. Create a Target Profile; 6. Determine, Analyze and Prioritize Gaps; 7. Implement Action Plan. The following are key components integral to these steps:
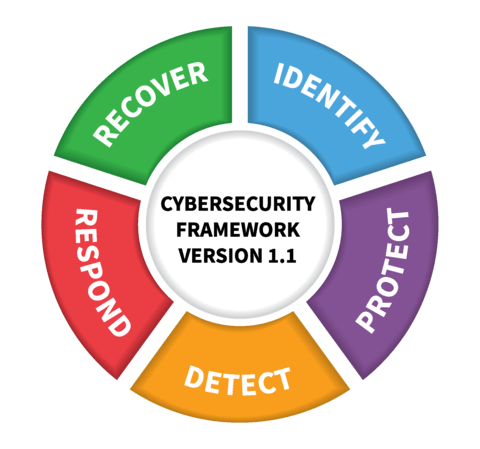
The Framework Core, which defines five functions (Identify, Detect, Protect, Respond, Recover), each containing Categories and Sub-categories of tasks and sub-tasks. For example, the Identify Function includes the Category, Supply Chain Risk Management (SCRM), which consists of multiple Sub-categories. For the Identify SCRM Category, one Sub-category task is: “Suppliers and third-party partners of information systems, components, and services are identified, prioritized, and assessed using a cyber supply chain risk assessment process.”
Each Sub-category, in turn, refers to multiple “Information References” consisting of detailed “how to” tasks that provide detailed information on how to meet this requirement. The CSF points to Information References for several other frameworks. This serves as a cross-mapping, which enables the overlay, or translation, capability. The granularity in the Information References provides flexibility and varying degrees of rigor so that it can be effective for most private and public sector organizations, despite differences in the existing framework, the organization’s size, complexity or required rigor for the intended security posture.
Implementation Tiers: The CSF proposes four levels of implementation similar to the notion of a maturity model. The highest level indicates the strongest implementation. An organization assigns Tiers to determine Current and Target Profiles. The gap between the two serves to define a roadmap that aligns
to the organization’s strategy and goals – stuff purse string holders really appreciate. This allows them to review and reflect on things like the legal/regulatory requirements and industry best practices… And to make informed resource allocation decisions for prioritizing risk management efforts – the gold that the CSF offers within a reasonable grasp.