By Kathryn Daily, CISSP, CAP, RDRP
Back in February, NIST issued a public Request for Information (RFI) to identify how the Cyber Security Framework was being used and also for recommendations on improving the effectiveness of the Framework and its alignment with other cyber security resources.
“Every Organization needs to manage cybersecurity risk as part of doing business, whether it is in industry, government, or academia… it is critical to their resilience and our nation’s economic security. There are many tools available to help, and the CSF is one of the leading frameworks for public sector cybersecurity maintenance. We want private and public sector organizations to help make it even more useful and widely used, including by small companies.” – Commerce Deputy Secretary Don Graves
In response to the RFI, NIST received more than 130 responses from industry, non-profit, individuals, government, and academia.
Once NIST received the responses they were grouped into themes based on commonalities. A total of 7 themes were identified, to wit:
1. Focus on maintaining and building on the key attributes with the update.
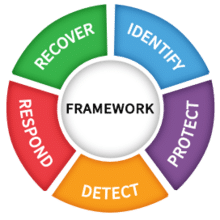
It was generally recognized that the CSF has been effective in helping organizations understand and manage cybersecurity risk as it’s flexible, easy-to-use and voluntary. That being said, many commenters requested avoiding changes to the fundamental structure of the CSF.
2. Align the CSF with existing efforts by NIST and others.
As CSF was created to provide a common organizational structure for standards, guidelines and practices, CSF supports coordination and communication within the US and internationally in an effort to strengthen cyber security. Since CSF 1.1 was released in 2018, NIST has updated several cyber resources such as the NIST SP 800-53 Rev. 5, The Privacy Framework, NICE Workforce Framework for Cyber Security, etc. Commenters recommended NIST provide guidance on how to use these frameworks and resources in concert with the CSF to achieve a more organized approach to cybersecurity.
3. Offer more guidance for implementing the CSF.
More than 500 references in the comments supported the need for more guidance on the implementation of CSF. CSF was designed to be vendor agnostic, scalable, and flexible to meet the needs of all sectors of private and public organizations. The CSF provides implementation guidance for various sectors through CSF profiles (I.e., manufacturing, election infrastructure, payroll, etc.). Comments requested that NIST offer more guidance on how to create profiles to align the CSF to more vertical markets than currently exist to aid in implementation of the CSF.
4. Ensure the CSF remains technology neutral but allows it to be readily ap-plied to different technology issues – including new advances and practices.
Comments here emphasized the need for the CSF to stay vendor neutral while also keeping up with new technology implementations such as cloud, hybrid work, and zero trust. Additionally, suggestions were made to have NIST provide guidance on how to address cybersecurity risks in IT, OT, and IoT.
5.Emphasize the importance of measurement, metrics, and evaluation using the CSF.
If you aren’t tracking your progress through metrics, how can you tell how effective your cybersecurity program is performing? Numerous respondents referenced a need for additional CSF guidance to support metrics and measurement, describing an opportunity to im-prove measurement of cybersecurity risk management in the CSF Update.
6. Consider cybersecurity risks in supply chains in the CSF.
Supply Chain Risk Management has be-come a hot new topic in the cybersecurity field as it introduces a lot of risk into an organization. Commenters have suggested that NIST expand and improve the CSF to meet that need, rather than setting up an entirely different frame-work given the flexibility of the CSF to cover many sectors of industry.
7. Use the National Initiative for Improving Cybersecurity in Supply Chains (NIICS) to align practices and provide effective practices, guidance, and tools to bolster cybersecurity sup-ply chain risk management.
Along with Theme 6, many commenters suggested that NIST utilize the NIICS to include Supply Chain Risk Management into the CSF to address the need of companies to protect their supply chain. The general consensus was that having a single clearinghouse for guidance, templates, tools, and information sharing would be of great benefit.
