By Lon J. Berman, CISSP, RDRP
Information Security Continuous Monitoring (ISCM) is arguably the most important step in the Risk Management Framework (RMF), since it is here that we ensure a system’s level of risk is
maintained at an acceptable level over the long term. The recent initiative to establish Continuous Authorization to Operate, i.e., Authorization to Operate (ATO) with no fixed expiration date, has further increased the dependency on a strong, robust ISCM program.
ISCM Publications
The National Institute of Standards and Technology (NIST) remains the number one source of information on ISCM. The key ISCM-related publications are:
- NIST SP 800-137
Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations (09/30/2011) - NIST SP 800-137A
Assessing Information Security Continuous Monitoring (ISCM) Programs: Developing an ISCM Program Assessment (05/21/2020) - NISTIR 8212
ISCMA: An Information Security Continuous Monitoring Program Assessment (03/31/2021)
NIST Special Publication (SP) 800-137A
This publication describes an approach for the development of Information Security Continuous Monitoring (ISCM) program assessments that can be used to evaluate ISCM programs within federal, state, and local governmental organizations and commercial enterprises. An ISCM program assessment provides organizational leadership with information on the effectiveness and completeness of the organization’s ISCM program, including the review of ISCM strategies, policies, procedures, operations, and analysis of continuous monitoring data. The ISCM assessment approach can be used as presented or as the starting point for an organization-specific methodology. It includes example evaluation criteria and assessment procedures that can be applied to organizations.
NIST Interagency Report (IR) 8212
This publication describes an example methodology for assessing an organization’s Information Security Continuous Monitoring (ISCM) program. It was developed directly from NIST guidance and is applicable to any organization, public or private. It can be used as documented or as the starting point for a different methodology. Included with the methodology is a reference implementation (ISCMAx tool) that is directly usable for conducting an ISCM assessment.
ISCMAx Tool
The ISCMAx tool – available from the NISTIR 8212 publication details page at: https://csrc.nist.gov/publications/detail/nistir/8212/final under “Supplemental Material” – is intended for use as a companion tool when conducting ISCM Program Assessment Reviews. ISCMAx is a macro-enabled Microsoft Excel application, suitable for use on Windows-based systems. ISCMAx includes 128 “assessment elements.”
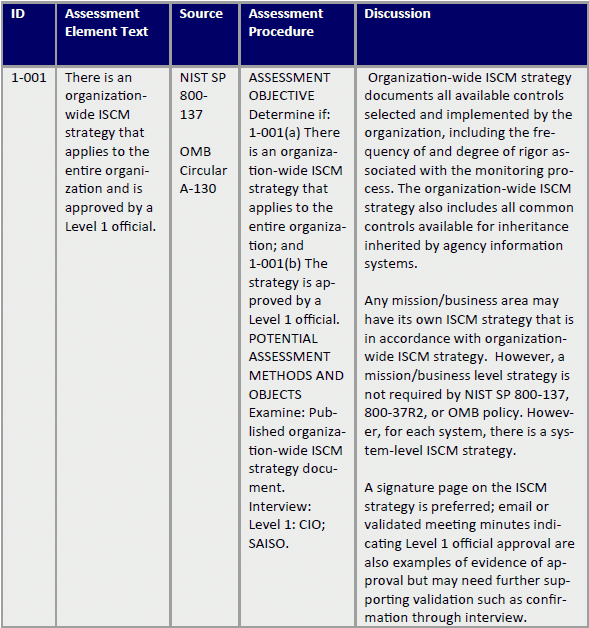
The ISCMAx spreadsheet includes assessment objectives and recommended assessment procedures for each assessment element, as shown in the example below:
The ISCMAx assessment can be applied at each of the three organizational “levels” defined by NIST:
Level 1 – organization-wide level
Level 2 – organizational unit/business process level
Level 3 – information system level
