Who should attend?
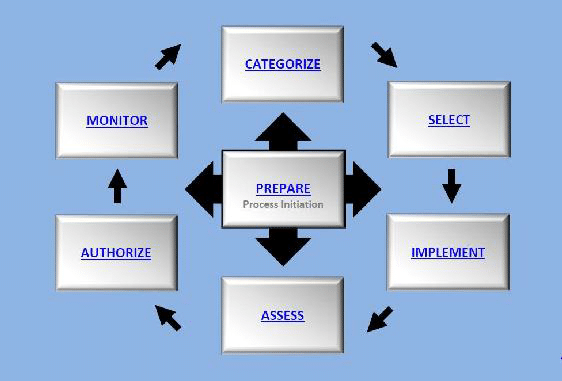
The RMF for Federal Agencies training program is suitable for employees and contractors of federal “civil” agencies and the intelligence community, as well as their supporting vendors and service providers. The full four-day program is recommended for most students. Managers and others who need only high-level knowledge of RMF have the option of attending just the RMF for Federal Agencies Fundamentals (one day).